Up to version 5.5 a vCenter appliance was usually deployed by importing the corresponding ovf template that could be downloaded from the VMware website. That process changed with version 6.0 since there is no longer an ovf template. Instead, VMWare provides and ISO image that contains the necessary data and tools to deploy a vCenter appliance, even directly from the command line.
After downloading the ISO image file from the my vmware portal mount it, e.g. to /mnt
# mount -o loop /var/lib/libvirt/images/VMware-VCSA-all-6.0.0-3343019.iso /mnt/
The vcsa command line deployment tool can be found at vcsa-cli-installer/lin64/vcsa-deploy. Since the available options and arguments to this tool are tucked away in one of the many vCenter documentation pdfs, here’s the output of vcsa-deploy --help
$ vcsa-cli-installer/lin64/vcsa-deploy --help
usage: vcsa-deploy install [-h] [--template-help] [-v] [-t]
[--log-dir LOG_DIR] [--verify-only]
[--skip-ovftool-verification] [--no-esx-ssl-verify]
[--sso-ssl-thumbprint SSL-SHA1-THUMBPRINT]
[--accept-eula]
template
Deploy vCSA to a remote host.
optional arguments:
-h, --help Show this help message and exit.
Other Arguments:
--template-help Print out the help for template settings.
-v, --verbose Debug information will be displayed in the console. If you set this parameter, you cannot set --terse.
-t, --terse Only warning and error information will be displayed in the console. If you set this paramter, you cannot set --verbose.
--log-dir LOG_DIR Directory for log and other output files.
--verify-only Perform only the basic template verification and OVF Tool parameter verification, but do not deploy the vCenter Server Appliance.
--skip-ovftool-verification
Deploy the vCenter Server Appliance directly through OVF Tool without performing parameter verification. Basic template verification will still be performed.
--no-esx-ssl-verify Skip the SSL verification for ESXi connections.
--sso-ssl-thumbprint SSL-SHA1-THUMBPRINT
Validates server certificate against the supplied SHA1 thumbprint.
--accept-eula Accept the end-user license agreement. This argument is required to deploy the appliance.
Required Arguments:
template Path of a JSON file that describes the vCenter Server Appliance deployment procedure.
Use --template-help for a list of template settings.
The exit codes and their meanings are:
0: Command ran successfully.
1: Runtime error.
2: Validation error.
You can find sample json templates for the deployment in vcsa-cli-installer/templates/install/. The options should be quite self-explanatory and cover
- Networking
- SSO
- System
- Database
- Deployment
A comprehensive list of valid parameters of the json file is available as well by invoking vcsa-cli-installer/lin64/vcsa-deploy --template -h
The deployment.option parameter specifies, how much virtual harware (CPUs, RAM) should be allocated for the vCenter appliance. Here’s a table of the available options (taken from the VMware vSphere 6.0 Documentation Center)
vCenter Server Appliance size
| Option | max. hosts | max. VMs | appliance CPUs | appliance Memory |
|---|---|---|---|---|
| tiny | 10 | 100 | 2 | 8 GB |
| small | 100 | 1.000 | 4 | 16 GB |
| medium | 400 | 4.000 | 8 | 24 GB |
| large | 1.000 | 10.000 | 16 | 32 GB |
Note that the hostname parameter in the network section needs to have a forward and reverse DNS entry (see VMware vCenter server 6 deployment guide) to work. An IP address is also fine though.
After editing the json file to reflect your configuration you can deploy the vCenter appliance by running vcsa-cli-installer/lin64/vcsa-deploy path_to_config_file.json --accept-eula
# vcsa-cli-installer/lin64/vcsa-deploy ~/vcenter.json --accept-eula
Performing basic template verification...
Starting vCenter Server Appliance installer to deploy
"vCenter-Server-Appliance"...
This appliance is a vCenter Server instance with an embedded Platform Services
Controller.
See /tmp/vcsaCliInstaller-2016-03-08-15-06-xXUT2j/vcsa-cli-installer.log for the
installer logs.
Run the installer with "-v" or "--verbose" to log detailed information
Running OVF Tool to deploy the OVF...
Opening vCenter Server Appliance image: /mnt/vcsa/vmware-vcsa
Opening VI target: vi://root@esxihost:443/
Deploying to VI: vi://root@esxihost:443/
Progress: 99%
Transfer Completed
Powering on VM: vCenter-Server-Appliance
Progress: 98%
Power On completed.
Waiting for IP address...
Received IP address: 172.30.0.23
Installing services...
vCSA firstboot: Progress: 5% Setting up storage
vCSA firstboot: Progress: 50% Installing RPMs
vCSA firstboot: Progress: 55% Installed
oracle-instantclient11.2-odbc-11.2.0.2.0.x86_64.rpm
vCSA firstboot: Progress: 63% Installed rvc_1.4.0-3196809_x86_64.rpm
vCSA firstboot: Progress: 64% Installed
VMware-rhttpproxy-6.0.0-3339084.x86_64.rpm
vCSA firstboot: Progress: 65% Installed
vmware-certificate-server-6.0.0.2457-3242066.x86_64.rpm
vCSA firstboot: Progress: 66% Installed
vmware-identity-sts-6.0.0.6360-3208448.noarch.rpm
vCSA firstboot: Progress: 67% Installed
VMware-cis-license-6.0.0-3242064.x86_64.rpm
vCSA firstboot: Progress: 70% Installed
vmware-esx-netdumper-6.0.0-0.0.2981910.i386.rpm
vCSA firstboot: Progress: 73% Installed
VMware-Postgres-9.3.9.0-2921310.x86_64.rpm
vCSA firstboot: Progress: 77% Installed
VMware-Postgres-plpython-9.3.9.0-2921310.x86_64.rpm
vCSA firstboot: Progress: 79% Installed
VMware-Postgres-client-jdbc-9.3.9.0-2921310.noarch.rpm
vCSA firstboot: Progress: 80% Installed VMware-invsvc-6.0.0-3242064.x86_64.rpm
vCSA firstboot: Progress: 81% Installed VMware-vpxd-6.0.0-3339084.x86_64.rpm
vCSA firstboot: Progress: 81% Installed
VMware-vpxd-client-6.0.0-3339084.x86_64.rpm
vCSA firstboot: Progress: 83% Installed
VMware-vpxd-vctop-6.0.0-3339084.x86_64.rpm
vCSA firstboot: Progress: 84% Installed
VMware-cloudvm-vimtop-6.0.0-3339084.x86_64.rpm
vCSA firstboot: Progress: 85% Installed ipxe-1.0.0-1.2882051.vmw.i686.rpm
vCSA firstboot: Progress: 86% Installed
vmware-autodeploy-6.0.0-0.0.3253919.noarch.rpm
vCSA firstboot: Progress: 86% Installed VMware-sps-6.0.0-3339084.x86_64.rpm
vCSA firstboot: Progress: 87% Installed VMware-vdcs-6.0.0-3242353.x86_64.rpm
vCSA firstboot: Progress: 89% Installed
VMware-vsanmgmt-6.0.0-0.1.3339084.x86_64.rpm
vCSA firstboot: Progress: 90% Installed vmware-vsm-6.0.0-3339084.x86_64.rpm
vCSA firstboot: Progress: 90% Installed vsphere-client-6.0.0-3338001.noarch.rpm
vCSA firstboot: Progress: 91% Installed
VMware-perfcharts-6.0.0-3339084.x86_64.rpm
vCSA firstboot: Progress: 95% Configuring the machine
Services installations succeeded.
Configuring services for first time use...
vCSA firstboot: Progress: 3% Starting VMware Authentication Framework...
vCSA firstboot: Progress: 10% Starting VMware Identity Management Service...
vCSA firstboot: Progress: 17% Starting VMware Component Manager...
vCSA firstboot: Progress: 20% Starting VMware License Service...
vCSA firstboot: Progress: 24% Starting VMware Platform Services Controller
Client...
vCSA firstboot: Progress: 27% Starting VMware Service Control Agent...
vCSA firstboot: Progress: 31% Starting VMware vAPI Endpoint...
vCSA firstboot: Progress: 34% Starting VMware System and Hardware Health
Manager...
vCSA firstboot: Progress: 37% Starting VMware Appliance Management Service...
vCSA firstboot: Progress: 44% Starting VMware Common Logging Service...
vCSA firstboot: Progress: 48% Starting VMware Postgres...
vCSA firstboot: Progress: 55% Starting VMware Inventory Service...
vCSA firstboot: Progress: 58% Starting VMware Message Bus Configuration
Service...
vCSA firstboot: Progress: 63% Starting VMware vSphere Web Client...
vCSA firstboot: Progress: 64% Starting VMware vSphere Web Client...
vCSA firstboot: Progress: 65% Starting VMware vSphere Web Client...
vCSA firstboot: Progress: 68% Starting VMware ESX Agent Manager...
vCSA firstboot: Progress: 72% Starting VMware vSphere Auto Deploy Waiter...
vCSA firstboot: Progress: 75% Starting VMware vSphere Profile-Driven Storage
Service...
vCSA firstboot: Progress: 79% Starting VMware Content Library Service...
vCSA firstboot: Progress: 82% Starting VMware vCenter Workflow Manager...
vCSA firstboot: Progress: 89% Starting VMware vService Manager...
vCSA firstboot: Progress: 93% Starting VMware Performance Charts...
vCSA firstboot: Progress: 96% Starting vsphere-client-postinstall...
First time configuration succeeded.
vCenter Server Appliance installer finished deploying
"vCenter-Server-Appliance".
This appliance is a vCenter Server instance with an embedded Platform Services
Controller.
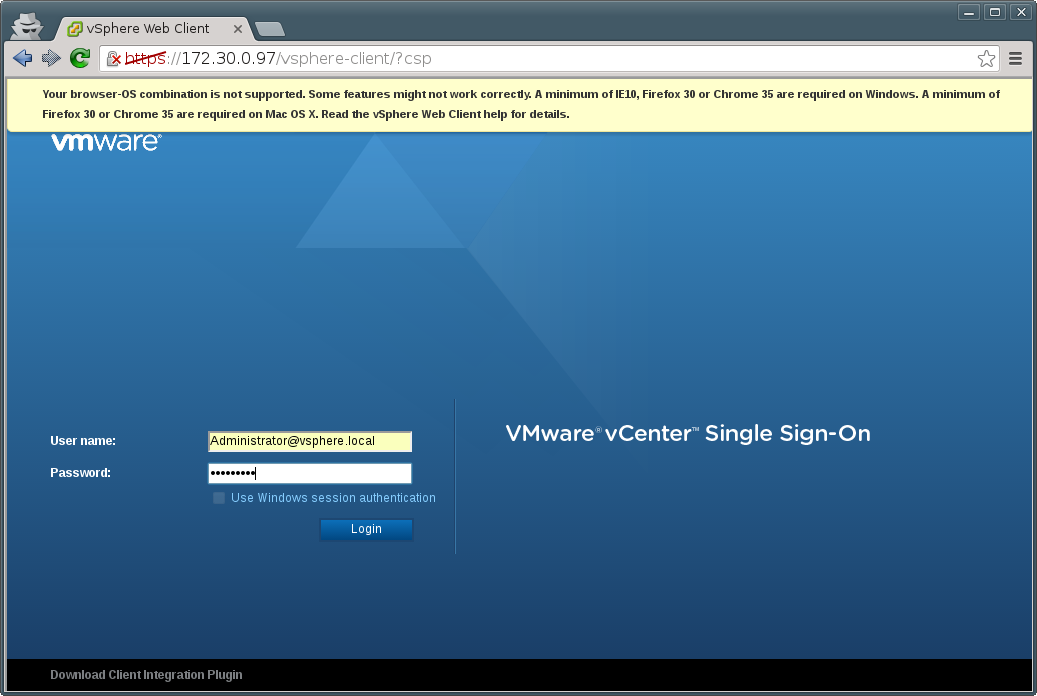
System Name: 172.30.0.97
Log in as: Administrator@vsphere.local
Finished successfully.
You should now be able to long into the vSphere Web Client with Administrator@vsphere.local as username and the password you specified in the json file
You can safely ignore the warning about the browser-OS combination.